Secure Software Core Requirements
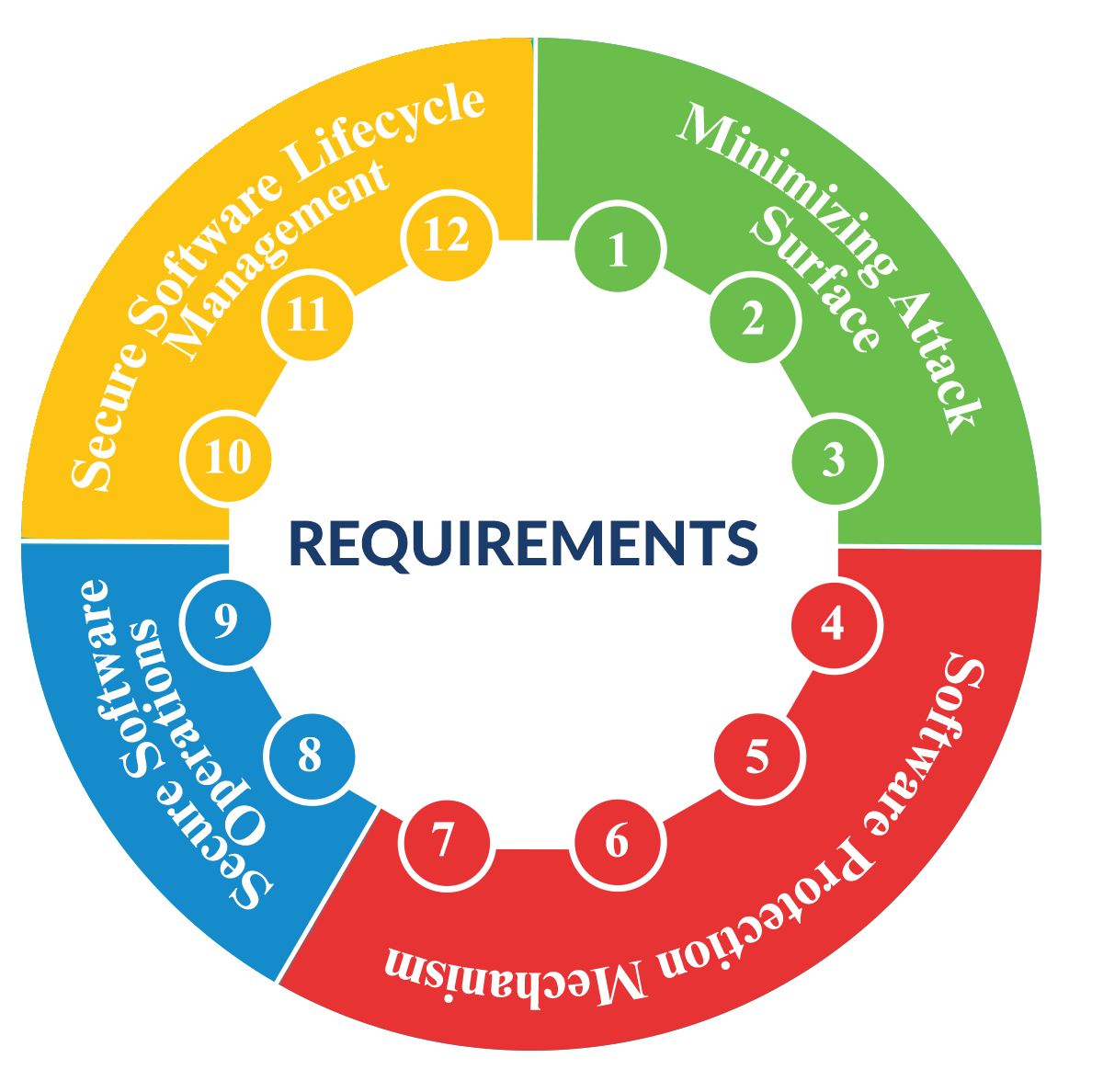
PCI SSS is the revised version for the previous PA DSS standard The new standard is coupled with PCI SLC to form PCI SSF altogether. The standard applies to the security characteristics, controls,features, and functionalities that payment software must possess and maintain throughout its lifecycle.
Secure Software Standards consist of two parts,
-
-
Module A Account Data Protection.
The standard focuses on ensuring that applications are maintained in a manner that protects payment transactions and data, minimizing the vulnerabilities, and defending itself from any security attacks.
Validation against PCI SSS helps assure that Payment Software is developed with security to protect the integrity of the software and the confidentiality of sensitive data it captures, stores, processes, and transmits. Adhering to PCI SSS will ease the organization to verify the software is properly configured and meets applicable PCI DSS requirements.
What We Offer
The key to implementing robust security controls lies in identifying the right scope, recognizing the difference between compliance and security and in sustaining compliance after successful control implementation.

 +91 9594449393
+91 9594449393 +1 4847906355
+1 4847906355 +63 9208320598
+63 9208320598 +44 1519470017
+44 1519470017 +84 908370948
+84 908370948 +7 9639173485
+7 9639173485 +62 81808037776
+62 81808037776 +90 5441016383
+90 5441016383 +66 993367171
+66 993367171 +254 725235855
+254 725235855 +256 707194495
+256 707194495 +46 700548490
+46 700548490.png)


