POS Device Security and the Cleanliness.
POS devices and their usage have become an integral part of every customer facing business....
POS Terminal Application Security Testing ascertains to the identification of possible/existing threats and security bugs that would compromise the system and would allow unauthorized persons or systems to access private information stored on the device. Owing to the significant growth in the usage of payment cards in monetary transactions, POS devices play a fundamental role in the entire transaction cycles, managing card data and other sensitive details.
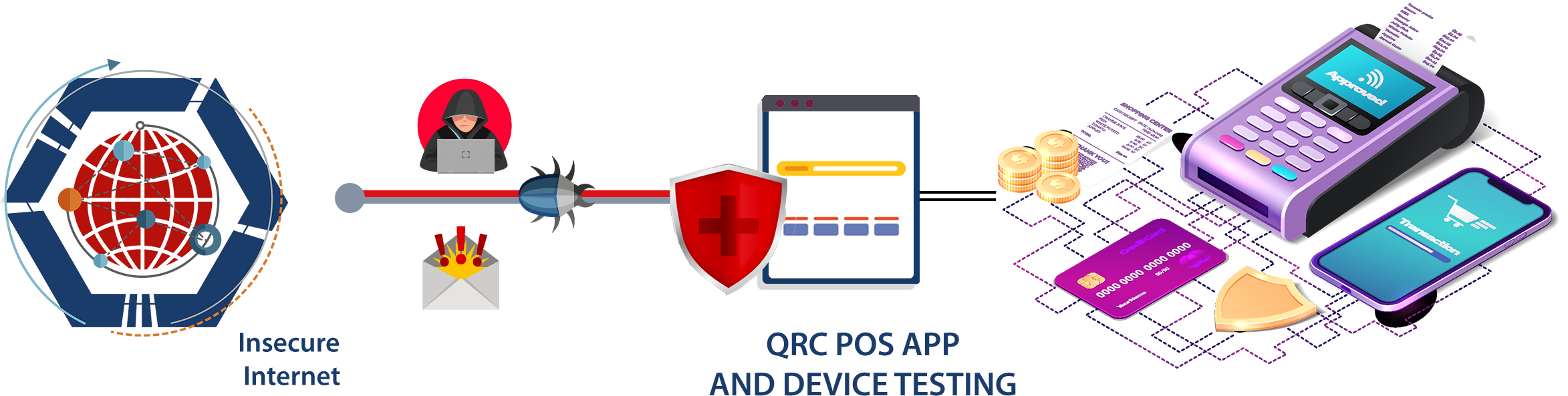
Hence, it becomes vital for these devices to undergo thorough security assessments even on upgrades at the software level.These testing assist developers in remediating the security bug from the POS Device and application and make the device safe from any unauthenticated or unauthorized actions which can cause an impact on the organization..
Regular assessments as such help safeguard both the hardware and the software application from any unauthorized access which can cost the organization both in reputation and resources