The term "VAPT" (vulnerability assessment and penetration testing) refers to the process of identifying security flaws and potential exploits that could be used by unauthorized users to impact a target organization's environment, steal sensitive or financial data, or take control of user accounts.
A vulnerability can be defined as a bug in code or a flaw in software design that can be exploited to cause harm or a gap in security procedures or a weakness in internal controls that when exploited results in a security breach.
Security assessment can be carried out on publicly accessible or internal systems for the environment's physical systems as well as that uses various cloud service providers.
The evaluation of the system components helps to understand the security posture and the effectiveness of the security defenses of the organization. The resulting exhaustive report includes the critical finding that can help organizations evade another security incident.
Importance of VAPT Testing Services in Organizations
Conducting routine security audits, can be instrumental in uncovering the underlying vulnerabilities of your website's security configurations. The use of VAPT services is mandated by law in several sectors to ensure compliance with present regulations. For instance, PCI DSS mandates certified security professionals to conduct both internal and external penetration tests.
Vulnerability Assessment and Penetration Testing (VAPT) services are essential for organizations because they:
- Identify vulnerabilities and security weaknesses, thereby aid in mitigating risks and prioritizing security efforts.
- Evaluate the efficacy of the current security measures.
- Ensure compliance with IT regulations, protecting sensitive data and reputation.
- Improve incident response and offer third-party assurance.
- Provide a competitive advantage.
- Help businesses adapt to the evolving threat landscape.
- Save costs and ensure business continuity.
What is included in VAPT Testing Services?
VAPT gives organizations a more complete application assessment than any single test. VAPT provides a company with a more complete picture of its application risks, helping it safeguard its information and systems from harmful assaults. Most vulnerabilities in third-party and internal software can be patched. While a VAPT provider finds and classifies vulnerabilities, IT security teams can focus on important issues.
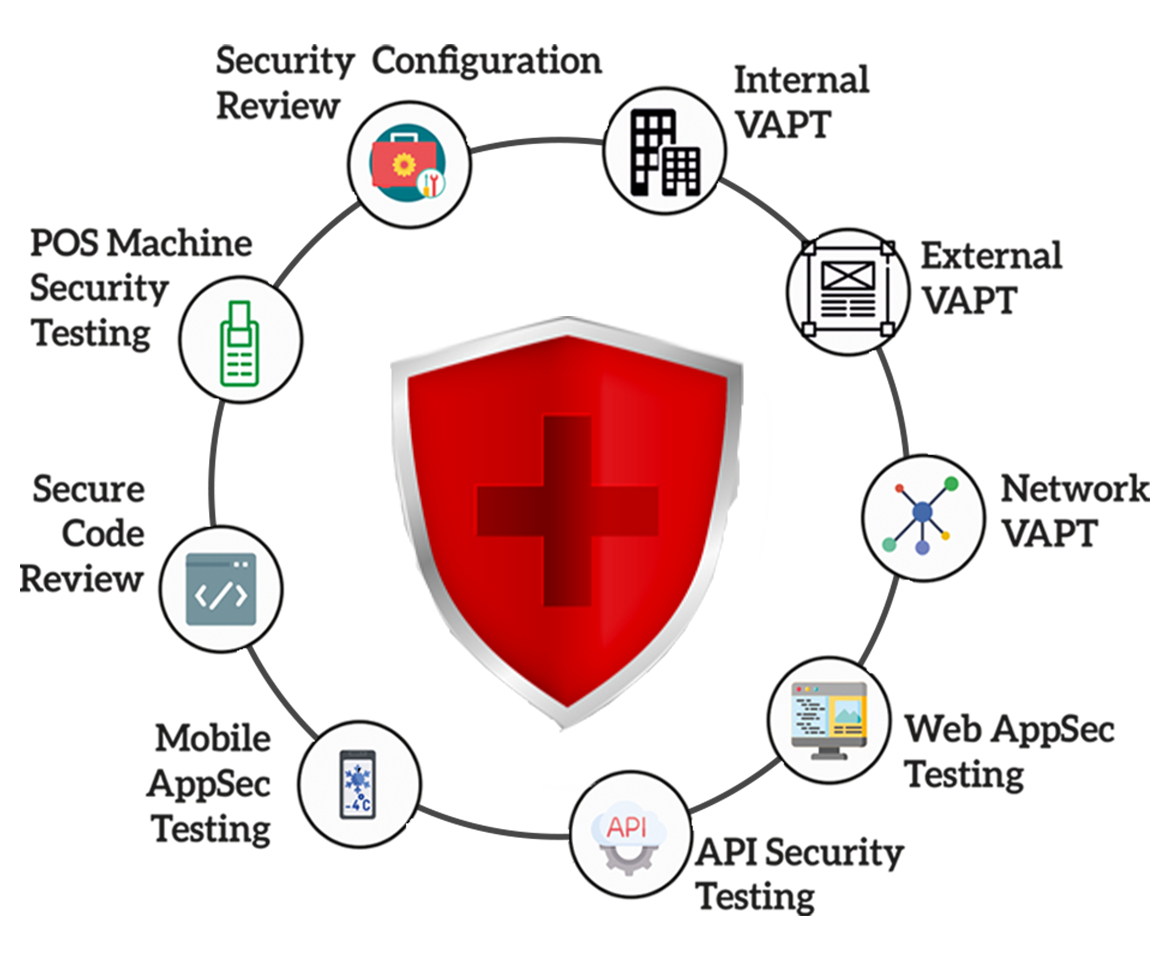
Our VAPT Services includes, but not limited to:
- Web & Mobile Application Security Testing: Application security testing detects application vulnerabilities, covers online and mobile app services and reduces risks for regulatory compliance.
- API Security Testing: API security testing is a process that aims to find, categorize, and exploit possible vulnerabilities inside Application Programming Interfaces (APIs) and Web Services.
- POS Terminal Application Security Testing: The objective of POS Terminal Application Security Testing is to identify potential or existing vulnerabilities and security flaws that might jeopardize the system's integrity and enable unauthorized individuals or systems to get access to sensitive information stored on the device.
- PCI Network Segmentation Penetration Testing: The primary objective of conducting network segmentation penetration testing for PCI-DSS is to assess and verify the efficacy of network traffic controls implemented between distinct segments, namely those connecting out-of-scope networks to in-scope networks that store sensitive information.
- Network & Server Security Assessment - At its core, a network security assessment seeks to pinpoint security vulnerabilities and offer suggestions for enhancement. Through a comprehensive analysis of your network security, you can verify that your organization is ready to face potential cyber threats and reduce the risk of cybersecurity breaches.
Types of Vulnerability Assessment and Penetration Testing
Keep in mind that the VAPT expense varies depending on the kind of security audit that the company does. The following are a few typical VAPT service categories that are provided by current businesses.
- Approach-based VAPT services: Black-box, white-box, and gray-box testing are other categories into which approach-based VAPT services can be separated.
- Methodology-based VAPT services: This pentest includes various evaluations and tests. VAPT professionals identify enterprise IT security vulnerabilities. Based on vulnerabilities, the organization takes corrective actions.
Why choose QRC for VAPT Testing Services?
At QRC, we are not just a Vulnerability Assessment and Penetration Testing (VAPT) service provider, our focus is on providing an entire Risk Management service to our clients. We serve as your allies in the world of cyber defense. Our organization provides a comprehensive selection of security assessment services and guidance for enhancing your security teams, and continuous monitoring of security risks in real time.
- Knowledge and Experience: Our team comprises of of qualified professionals with industry certifications such as CISSP, CISA, PCI QSA, PA QSA, PCI-SSF QSA, 3DS Assessor, OSCP, ISO/IEC 27001 LA, ISO/IEC 27701 LA, COBIT, CEH, CHFI, and others. QRC professionals are skilled in identifying weak points and developing strong security solutions that keep digital assets safe and businesses compliant.
- Tailored Approach and Custom Solutions: We realize that every business has different security requirements. Whether you're in the healthcare or banking sectors, our VAPT services will be tailored to your unique needs and infrastructure.
- Proactive Security: We provide proactive cybersecurity advice and solutions to protect your digital infrastructure beyond just discovering vulnerabilities. Our strategy focuses on assisting businesses in fortifying their defenses.
- Risk Mitigation: QRC's VAPT services help you stay compliant with laws, protect your reputation, and lessen the likelihood of a security breach.
- Client-Centric Approach: Our top priorities are effective communication, teamwork, and your satisfaction. Our client-centric approach guarantees that you are kept informed and engaged throughout the assessment process. Our reports are easy to read and understand, and they include details about the vulnerabilities we found, their severity, and how to fix them.
Our services include a thorough evaluation and ongoing surveillance aimed at identifying pre-existing weaknesses and vulnerabilities. We function as cyber detectives, discerning vulnerabilities inside infrastructure that may potentially facilitate a cyber assault, and afterwards suggesting strategies to effectively mitigate these risks.